When a cyberattack takes down your TMS, WMS, or other supply chain software (it’s a question of when, not if), will you be ready to respond as effectively as possible or will everyone on your team look at each other and frantically ask, “What do we do now?”
I wrote that back in June 2024 in a post titled, “When A Cyberattack Takes Down Your Supply Chain Software.“
This week, Starbucks, Sainsbury’s, Morrisons, and other companies are learning how prepared they are to deal with a cyberattack on one of their supply chain software vendors — specifically, Blue Yonder, which is dealing with a ransomware attack at the moment. As reported by CNN, the attack is “affecting a private cloud computing service the company provides some customers, but not the company’s public cloud environment.”
“Morrisons, which has about 1,600 convenience stores and 500 supermarkets across the U.K., said the outage affected its warehouse management systems for fresh foods and produce,” as reported by the Wall Street Journal. The article also reports that the attack has disrupted Starbucks’ ability “to pay baristas and manage their schedules, leaving cafe managers to manually calculate employees’ pay.”
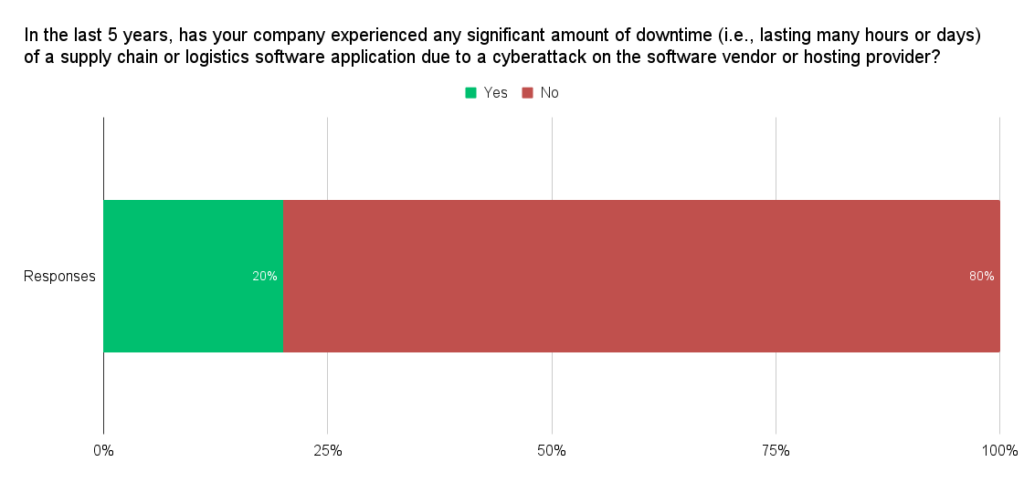
In the last 5 years, has your company experienced any significant amount of downtime (i.e., lasting many hours or days) of a supply chain or logistics software application due to a cyberattack on the software vendor or hosting provider?
We asked members of our Indago supply chain research community — who are all supply chain and logistics executives from manufacturing, retail, and distribution companies — that question in a June 2024 survey.
Most of our member respondents (80%) have not experienced any significant downtime of a supply chain or logistics software application due to a cyberattack in the last 5 years. In one case, however, a supply chain executive shared that their “major freight carrier was hacked with ransomware placed on their system. Initial impact on our business was around 4-5 weeks. They seemingly fixed the issue and then got hit again about 5 months later.”
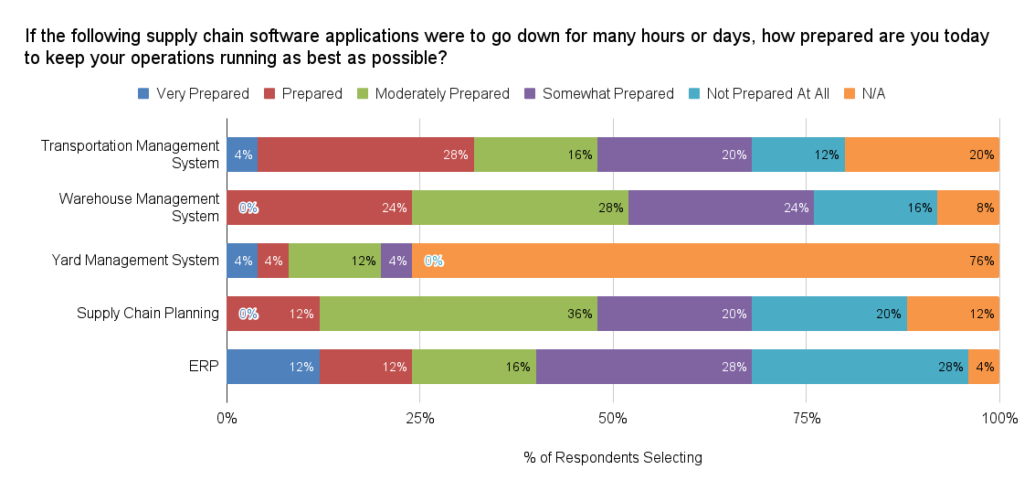
More than half the respondents (56%) said that they are only “Somewhat Prepared” (28%) or “Not prepared at all” (28%) to keep their operations running as best as possible if their ERP were to go down for many hours or days due to a cyberattack. 40% said the same thing about their Supply Chain Planning and Warehouse Management solutions going down, and 32% about their Transportation Management System.
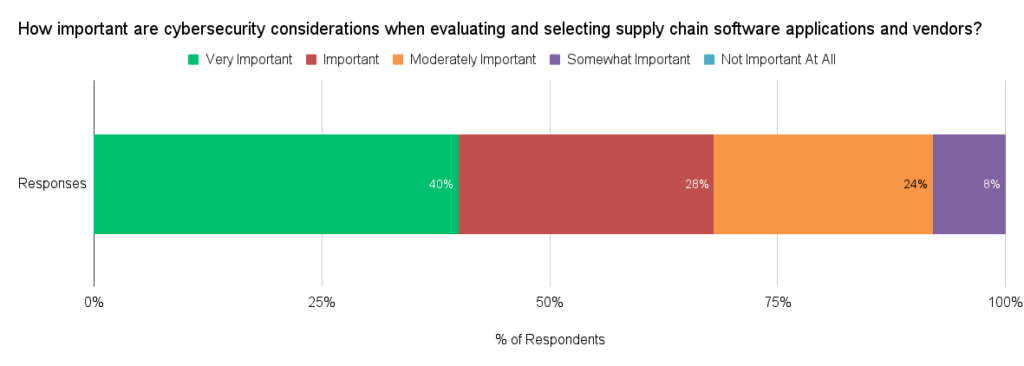
We also asked our members, “How important are cybersecurity considerations when evaluating and selecting supply chain software applications and vendors?” More than two thirds of the respondents (68%) said that cybersecurity considerations are either “Very Important” (40%) or “Important” (28%) when evaluating/selecting supply chain software and vendors.
“We’ve been fortunate to not have experienced downtime related to a hack of a software vendor, but it really is only a matter of time until this occurs,” said one Indago supply chain executive. “It’s important to have mitigation strategies — including pen/paper and phone calls — to keep the business running, but it would be a massive step backwards from the way we run our day-to-day operations. I shudder at the thought of a [system going down for days] but that would likely be the case when this type of incident occurs.”
Here are some other comments submitted by our members:
“We have to trust that supply chain software vendors are allocating adequate resources to securing their products. Software security is not my specialty, so I look at [a software vendor’s] customer list to see what other companies are trusting them with their business. I think history shows that any system can be susceptible if it is targeted by talented hackers. It’s how the supply chain software company reacts and how effectively we can implement and sustain the contingency plans we have in place.”
“The impact of being down for hours is much lower than being down for several days or weeks. We might be able to deal with a day down; we have SAP outages caused internally that are not due to a cyberattack and we end up figuring it out with our BCPs, but if we were down for multiple days or weeks, we are much more vulnerable and it would have significant financial impact on the organization.”
“You hope that the vetting process was solid enough to weed out subpar software providers. It is still literally a question of an employee clicking on a phishing link that is well disguised to look like something legit. We have seen it at our organization. Someone receives an email that looks like the real deal and they click on it. The latest one I have seen personally is a DocuSign spoof. I do lots of DocuSigns weekly. I now have to confirm the email address and if it looks suspicious, we put it through an analysis program to determine if it is phishing or not. It only takes one click for someone to access the whole system.”
Indago members can download the report for additional insights from the research.
Do you believe it’s just a question of time until a cyberattack brings down one of your supply chain or logistics software applications? How confident are you that your supply chain software vendors have the right people, process, and technologies to minimize the risk of a cyberattack disruption? Do you know what actions they are taking to fortify their cloud services against cyberattacks? Post a comment and share your experience and perspective.
What are you waiting for? Join Indago today!
If you’re a supply chain or logistics practitioner from a manufacturing, retail, or distribution company — and you’re interested in learning from your peers — I encourage you to learn more about Indago and join our research community. It is confidential, there is no cost to join and the time commitment is minimal (2-4 minutes per week) — plus your participation will help support charitable causes like Breakthrough T1D (formerly JDRF), American Logistics Aid Network, American Cancer Society, Feeding America, and Make-A-Wish.










